winapi - What is the purpose of the pause x86 instruction and the loop in the GetSystemTimeAsFileTime function disassembly? - Stack Overflow
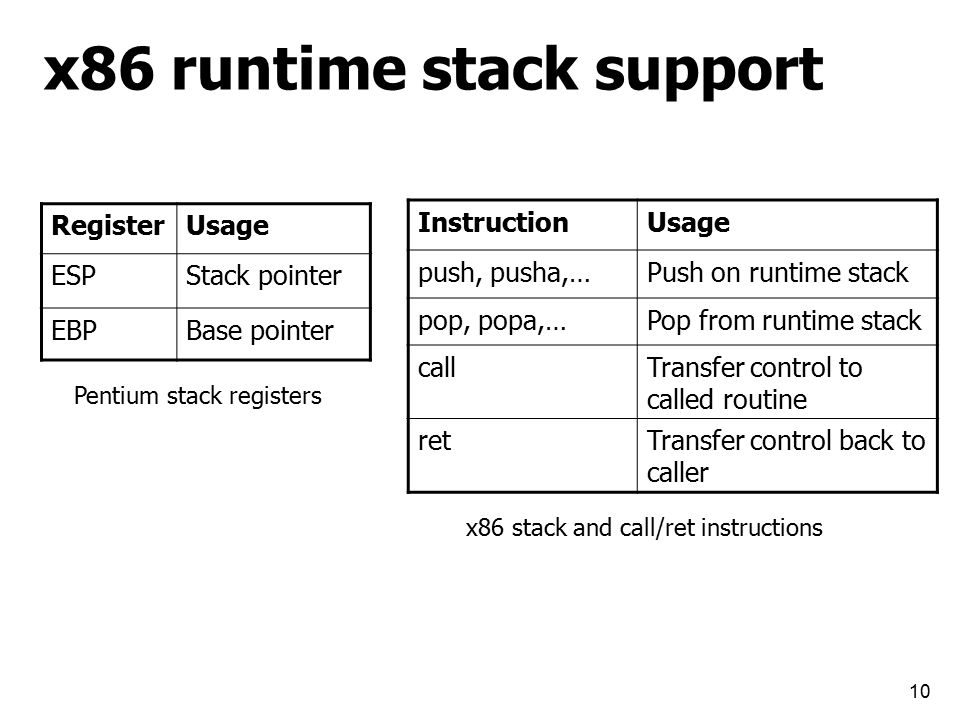
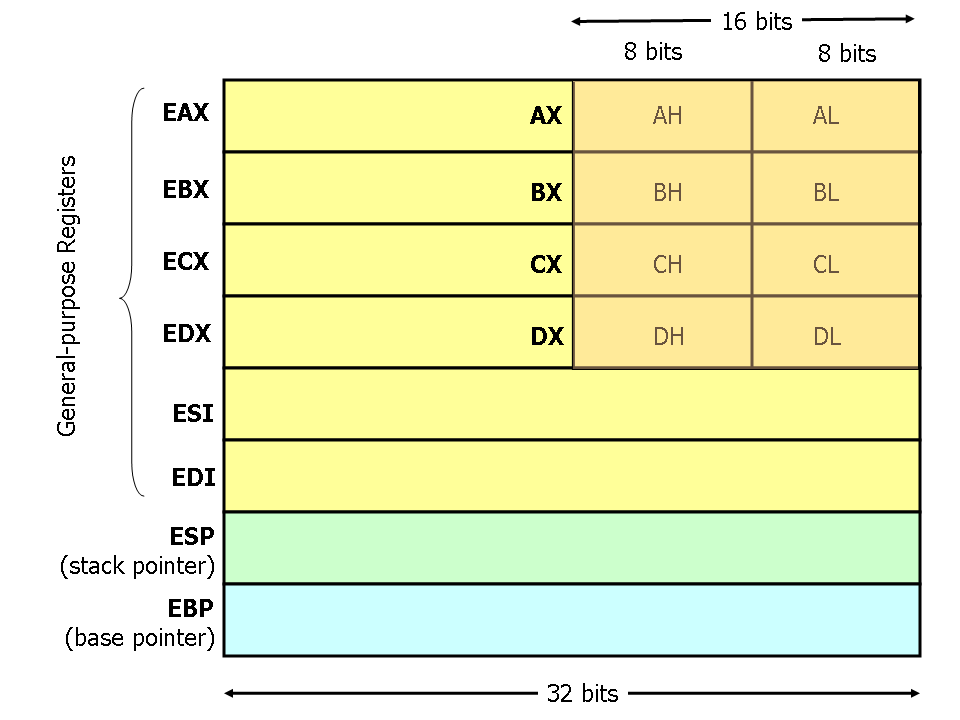
Winter Compiler Construction T11 – Activation records + Introduction to x86 assembly Mooly Sagiv and Roman Manevich School of Computer Science. - ppt download
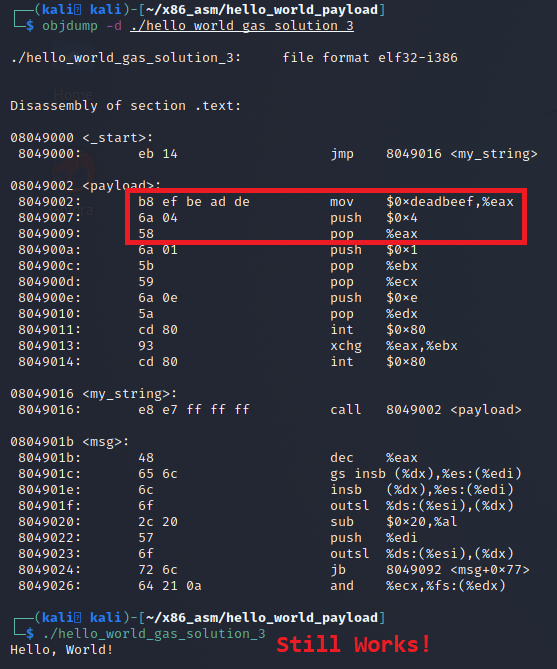
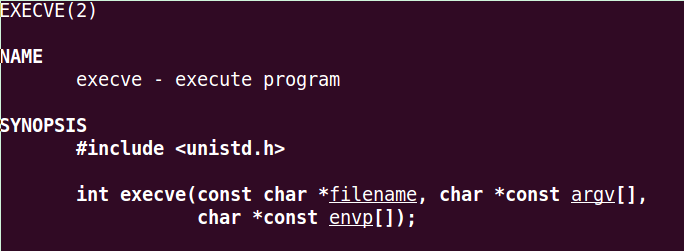
Linux X86 Assembly - How to Make Our Hello World Usable as an Exploit Payload - Professionally Evil Insights

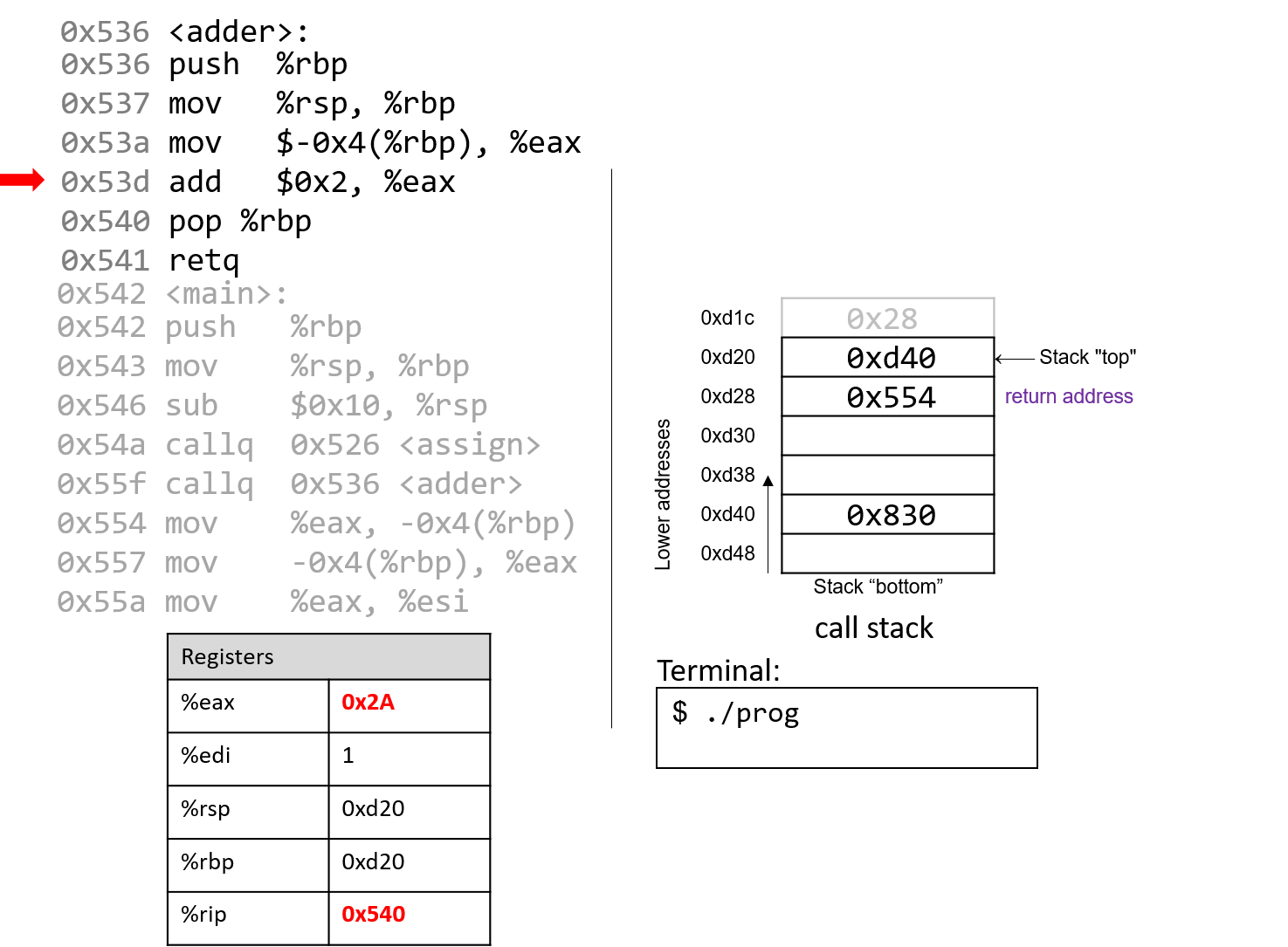
x86 - What happens exactly under the hood to Assembly `push`, `pop`, `call`, and `ret` operations? - Stack Overflow
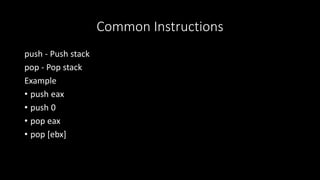
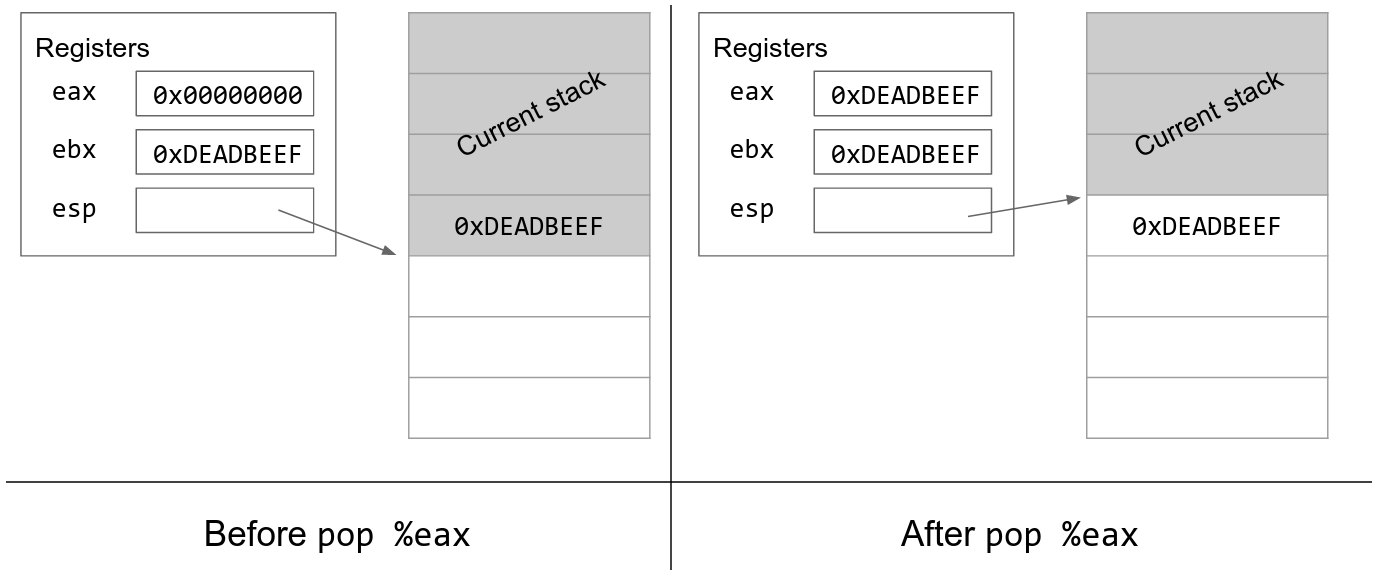
Outline The stack Push and pop instructions Offset-based stack accesses Argument and return registers Sharing registers Preservi
Incorrect PCode for x86 pop Instructions with Stack Pointer Operands · Issue #4282 · NationalSecurityAgency/ghidra · GitHub